Microsoft Azure Specific Information
Azure Marketplace Install
When logged into your Azure console, navigate to the [Heimdall offering] (https://portal.azure.com/#blade/Microsoft_Azure_Marketplace/MarketplaceOffersBlade/selectedMenuItemId/home/searchQuery/heimdall) or here:
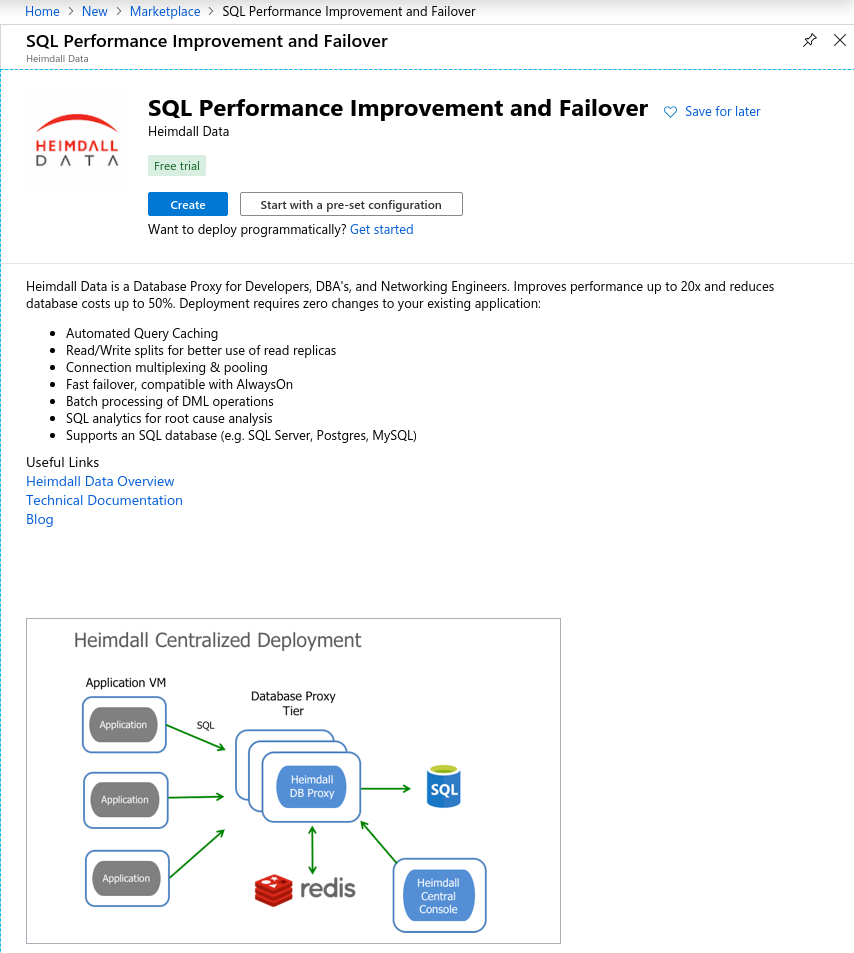
Configure the appropriate instance settings for your environment, and review/create:
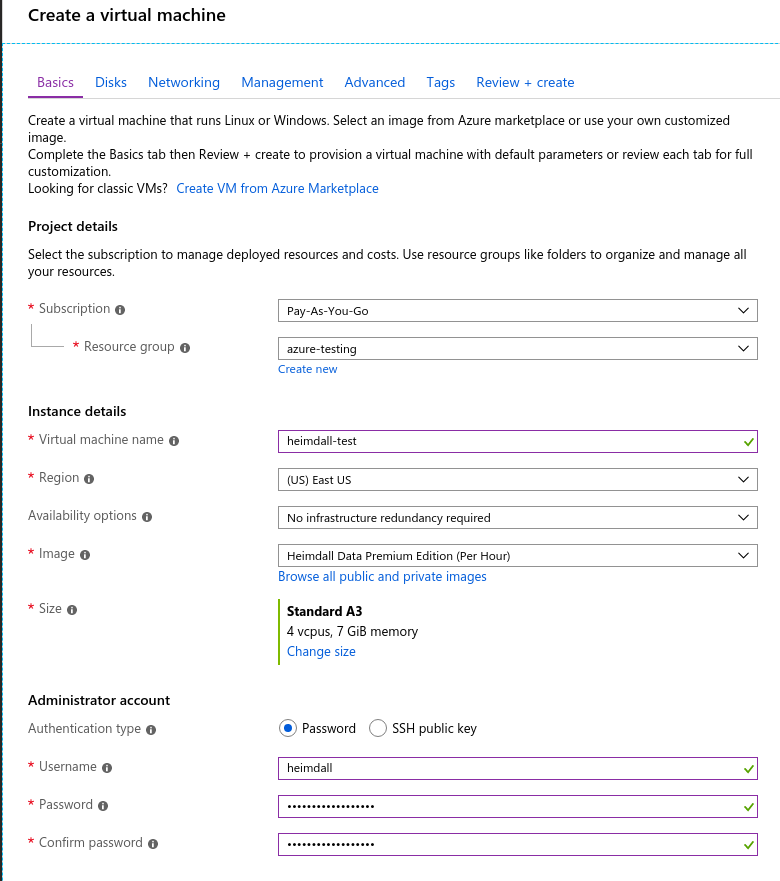
Review settings and create:
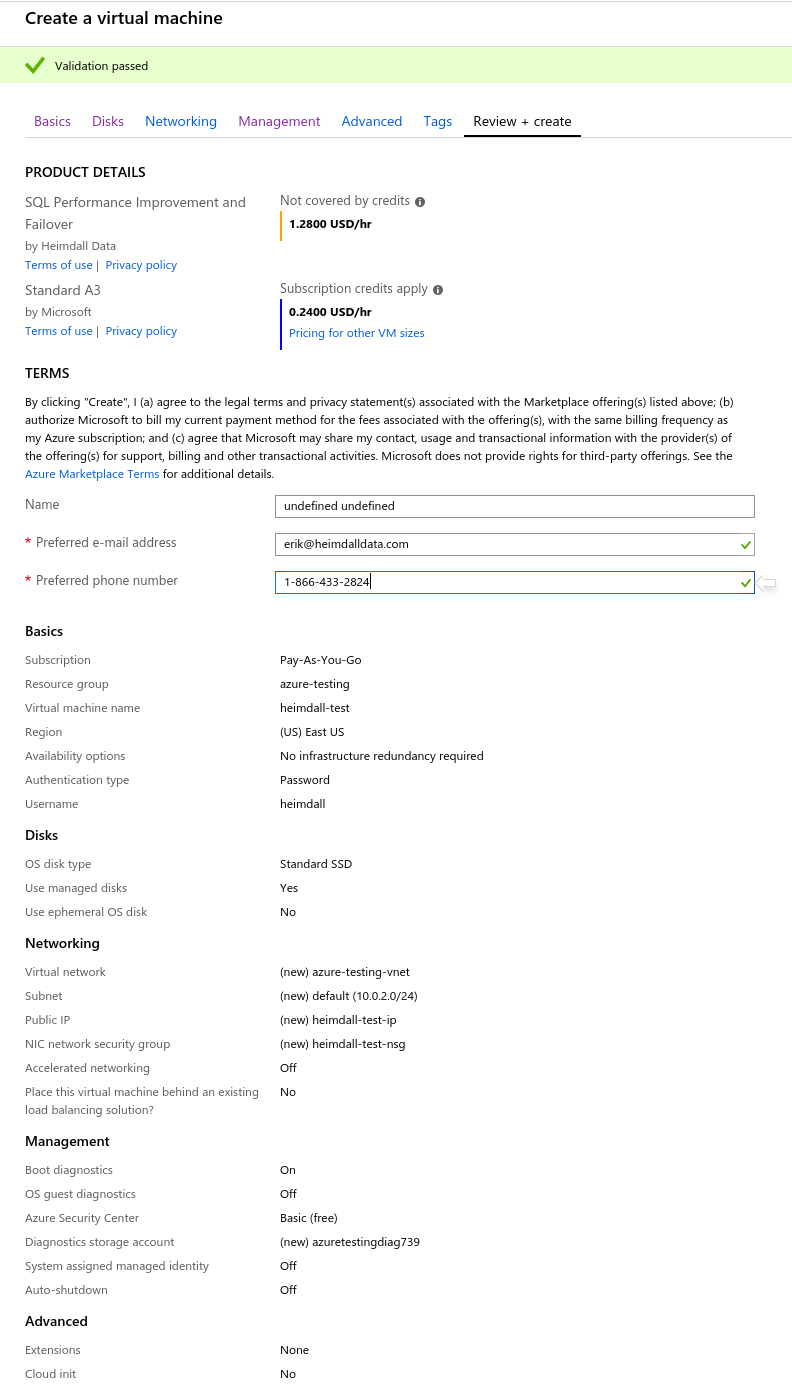
Once provisioned, review and adjust the instance networking settings to ensure that the appropriate ports are open, and unneeded ports are closed:
Once the instance is running, login via "admin" and "heimdall", then change the admin password:
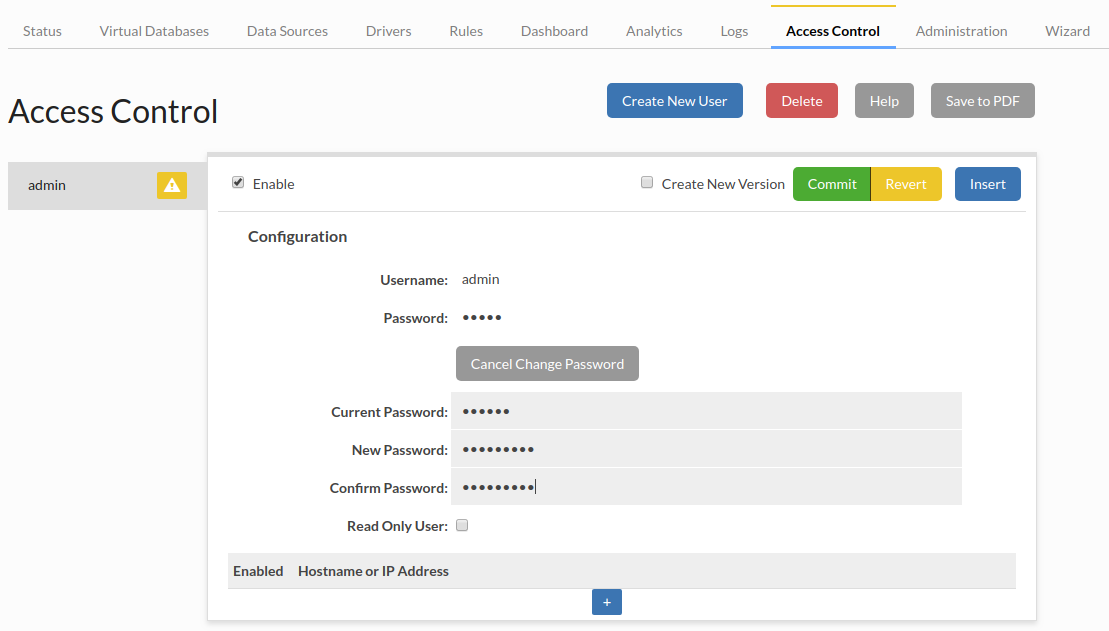
Finally, update the software to the newest release version (The Azure image does not automatically download updates):
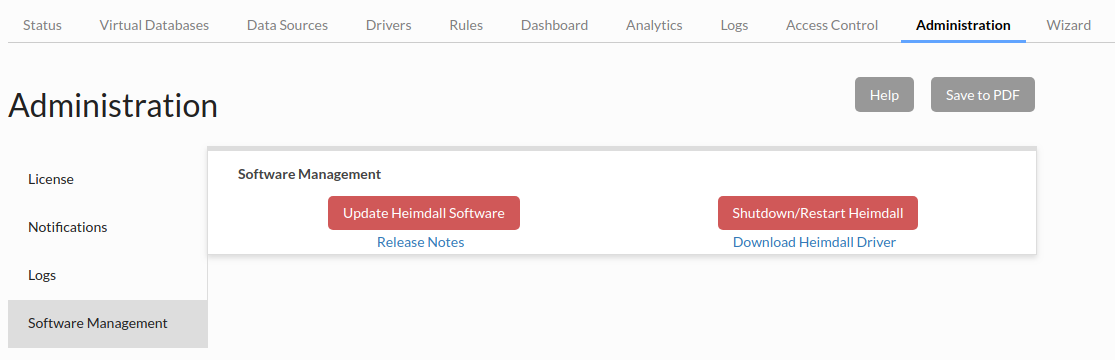
After a few minutes, refresh your browser (use ctrl-refresh if the UI appears broken), and check the server version, which should be at least 19.7.21.1.
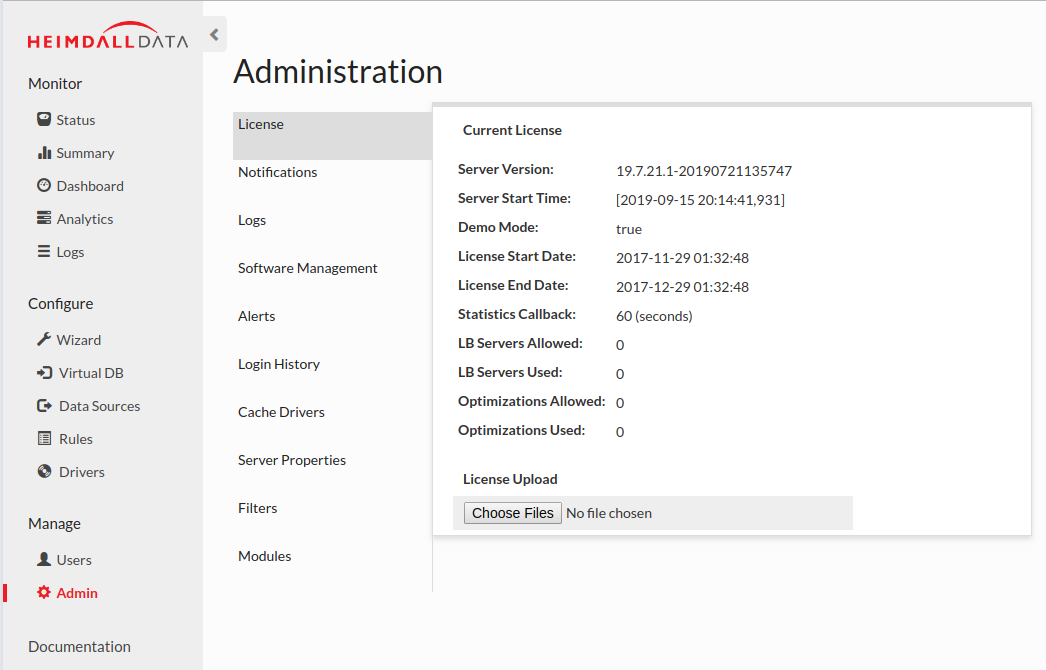
If the "LB Servers Allowed" is set to zero, please contact Heimdall support for a no-cost Azure Marketplace license, to disable notices about unlicensed usage, and upload via the "License Upload" option (as shown above).
Azure Managed Databases
When using the Azure Postgres or Azure MySQL managed databases, there is a requirement that the username used is of the format "user@hostname". Heimdall provides an option in the data source options of "azureDbHost", which if set to true, will automatically map the username to this format based on which server is being connected to. Ensure that when using this option, the fully qualified domain name is set in the JDBC URL.
SSL Note
With Postgres Azure, SSL is required, so in the connection properties, please set properties of "ssl=true" and "sslmode=require". Other SSL settings may work as well, but this is sufficient to ensure that the connectivity can be established.
Azure Cluster Tracking Limitations
HeimdallData does not support tracking cluster changes in Azure MySQL and Azure PostgreSQL (Azure-managed databases). This functionality is only supported for Azure Managed Instance (SQL Server).
Heimdall Azure VMSS Deployment Guide
This deployment script provisions a scalable, fault-tolerant Heimdall Proxy cluster on Azure using a Virtual Machine Scale Set (VMSS). It integrates with a pre-configured Heimdall Manager for full enterprise functionality.
Features Implemented
- VMSS based on Heimdall Azure Marketplace image
- Health probe on port 80, path
/status - Load balancer rule for a configurable proxy port (e.g.,
5432for Postgres) - Instance type:
Standard_D2s_v4 - Cloud-init startup script that generates
heimdall.confdynamically using: HEIMDALL_MANAGER_HOSTNAMEHEIMDALL_ACCESS_KEYHEIMDALL_SECRET_KEYHEIMDALL_VDBPROXY_PORT
Deployment Script
#!/bin/bash
set -e
# === Heimdall Configuration ===
BASELINE="heimdall-poc"
HEIMDALL_MANAGER_HOSTNAME="20.245.93.123"
# NOTE:
# Secrets can be securely retrieved from Azure Key Vault.
# Example (requires 'az login' or managed identity):
# HEIMDALL_ACCESS_KEY=$(az keyvault secret show --vault-name <vault-name> --name heimdall-access-key --query value -o tsv)
# HEIMDALL_SECRET_KEY=$(az keyvault secret show --vault-name <vault-name> --name heimdall-secret-key --query value -o tsv)
HEIMDALL_ACCESS_KEY="UX0jRZRDad28dRrK"
HEIMDALL_SECRET_KEY="6FQCFXBBHGMVJKmy"
HEIMDALL_VDB="azure-postgres-vdb"
PROXY_PORT=5432
RG="${BASELINE}-rg"
LOCATION="eastus"
VMSS_NAME="${BASELINE}-vmss"
LB_NAME="${BASELINE}-lb"
FRONTEND_IP="${BASELINE}-fe"
BACKEND_POOL="${BASELINE}-bepool"
PROBE_NAME="${BASELINE}-probe"
LB_RULE="${BASELINE}-lbrule"
NSG="${BASELINE}-nsg"
ADMIN_USER="azureuser"
VM_SIZE="Standard_D2s_v4"
VNET="${BASELINE}-vnet" # set to the vnet the manager is in, and likely the databases as well.
# === Cloud-init payload ===
CLOUD_INIT=$(cat <<EOF
#cloud-config
write_files:
- path: /etc/heimdall.conf
permissions: '0644'
content: |
hdHost=${HEIMDALL_MANAGER_HOSTNAME}
hdPort=8443
hdRole=proxy
hdSecretKey=${HEIMDALL_SECRET_KEY}
hdPassword=${HEIMDALL_SECRET_KEY}
hdUser=${HEIMDALL_ACCESS_KEY}
vdbName=${HEIMDALL_VDB}
secure=true
EOF
)
# === Provisioning Resources ===
az group create --name $RG --location $LOCATION
az network lb create --resource-group $RG --name $LB_NAME --sku Standard --frontend-ip-name $FRONTEND_IP --backend-pool-name $BACKEND_POOL --vnet-name $VNET --subnet ${BASELINE}-subnet
az network lb probe create --resource-group $RG --lb-name $LB_NAME --name $PROBE_NAME --protocol Http --port 80 --path /status --interval 10 --threshold 3
az network lb rule create --resource-group $RG --lb-name $LB_NAME --name $LB_RULE --protocol Tcp --frontend-port $PROXY_PORT --backend-port $PROXY_PORT --frontend-ip-name $FRONTEND_IP --backend-pool-name $BACKEND_POOL --probe-name $PROBE_NAME --idle-timeout 4 --enable-tcp-reset true
az network nsg create --resource-group $RG --name $NSG
az network nsg rule create --resource-group $RG --nsg-name $NSG --name AllowSSH --protocol Tcp --priority 1000 --destination-port-range 22 --access Allow
az network nsg rule create --resource-group $RG --nsg-name $NSG --name ${BASELINE}-AllowProxy --protocol Tcp --priority 1001 --destination-port-range $PROXY_PORT --access Allow
HEIMDALL_IMAGE=$(az vm image list --publisher heimdall-data --offer heimdall-data --sku heimdall-enterprise-plus --all --query "sort_by([?version!=''], &version)[-1].urn" -o tsv)
az vmss create --resource-group $RG --name $VMSS_NAME --image "$HEIMDALL_IMAGE" --vm-sku $VM_SIZE --instance-count 1 --authentication-type ssh --generate-ssh-keys --upgrade-policy-mode automatic --admin-username $ADMIN_USER --vnet-name ${VNET} --subnet ${BASELINE}-subnet --nsg $NSG --lb $LB_NAME --backend-pool-name $BACKEND_POOL --custom-data "${CLOUD_INIT}"
az monitor autoscale create --resource-group $RG --resource $VMSS_NAME --resource-type Microsoft.Compute/virtualMachineScaleSets --name ${BASELINE}-AutoScale --min-count 1 --max-count 5 --count 1
az monitor autoscale rule create --resource-group $RG --autoscale-name ${BASELINE}-AutoScale --condition "Percentage CPU > 60 avg 5m" --scale out 1
az monitor autoscale rule create --resource-group $RG --autoscale-name ${BASELINE}-AutoScale --condition "Percentage CPU < 30 avg 10m" --scale in 1
LB_PROBE_ID=$(az network lb probe show --resource-group $RG --lb-name $LB_NAME --name $PROBE_NAME --query "id" -o tsv)
echo "Deployment complete. Proxy private endpoint (internal only):"
az network lb frontend-ip show --resource-group $RG --lb-name $LB_NAME --name $FRONTEND_IP --query "privateIpAddress" -o tsv
Post-Deployment Validation
After deployment:
- Access your proxy via the public IP on port
${PROXY_PORT} - VMs failing
/statuson port 80 will be replaced automatically - Scaling is based on average CPU load
Debugging Tips
SSH into the VM via the public IP:
#### Get logs from cloud-init
sudo tail -n 100 /var/log/cloud-init.log
sudo tail -n 100 /var/log/cloud-init-output.log
#### Confirm Heimdall is running
sudo systemctl status heimdall
Cleanup
To remove all resources:
az group delete --name $RG --yes --no-wait